In the age of artificial intelligence, digital identity, biometric verification, and advanced computer vision, privacy and data protection are more important than ever. Companies around the world rely on face recognition to authenticate users, secure access, enable automation, detect liveness, and enhance user experience using homomorphic encryption in Face Recognition. Yet at the same time, they must comply with strict privacy standards like GDPR, CCPA, DPA, and internal enterprise security policies.
This is where Homomorphic Encryption (HE) becomes revolutionary.
For the first time, organizations can perform face recognition on encrypted data without ever decrypting it. This solves one of the biggest challenges in AI security: How can we process biometric data while ensuring it is never visible to anyone?
At Faceplugin, one of our core research directions is designing privacy-preserving AI systems, including homomorphically encrypted face recognition, encrypted face embeddings, privacy-safe liveness detection, and secure on-device computation. This article provides an in-depth, readable explanation of how Homomorphic Encryption works, why it matters, and how it transforms the future of face recognition.
This blog is intentionally detailed and approximately 4,000 words, designed for companies, developers, and security officers evaluating next-generation biometric technology.
1. Introduction: Why Privacy Matters in Face Recognition
Modern face recognition systems are now deployed in:
-
Banking (KYC verification, fraud prevention)
-
Airports and border control
-
Smartphone authentication
-
E-commerce account verification
-
Enterprise access control
-
Attendance and workforce management
-
Smart home security
-
Retail and self-checkout
-
Government and public safety
-
Healthcare identity management
While face recognition unlocks speed, security, and automation, it introduces a crucial challenge:
Biometric data is sensitive and cannot be replaced.
If a password leaks, it can be changed.
If a credit card leaks, it can be replaced.
If a fingerprint or face template leaks, the damage is permanent.
As organizations adopt face recognition, they must confront questions like:
-
How can we process face embeddings without exposing raw biometric data?
-
How can we verify identities while respecting user privacy?
-
How can companies protect themselves from insider threats and data breaches?
-
How do we meet strict privacy laws that prohibit sending biometric data to external servers?
-
Can we perform face recognition securely in the cloud?
Homomorphic Encryption provides a powerful answer.
2. What is Homomorphic Encryption? A Simple Explanation
Homomorphic Encryption (HE) is a form of encryption that allows computations to be performed on encrypted data.
Unlike traditional encryption, where data must be decrypted before use, HE enables:
Encryption → Computation on Encrypted Data → Encrypted Results → Decryption Only by the End User
The server performing the computation never sees the actual data.
Example (Simple Concept):
Let’s say you want to verify two values, A and B.
-
You encrypt A → A’
-
You encrypt B → B’
The server receives only A’ and B’, which look like random noise.
The server then performs:
The server returns an encrypted result C’, which only the client can decrypt.
The server never knows A, B, or C.
This is the foundation behind homomorphically encrypted face recognition.
3. Types of Homomorphic Encryption
There are three major forms of HE, each with different capabilities.
3.1 Partial Homomorphic Encryption (PHE)
Allows limited operations (e.g., addition OR multiplication, but not both).
Useful for simple data processing.
3.2 Somewhat Homomorphic Encryption (SHE)
Allows more operations but still limited by computational complexity.
3.3 Fully Homomorphic Encryption (FHE)
Supports any arbitrary computation on encrypted data.
This is the holy grail of privacy-preserving computation.
Faceplugin’s research focuses on FHE-compatible face recognition, enabling highly secure, enterprise-grade biometric computation.
4. How Homomorphic Encryption Changes Face Recognition
Traditional face recognition works like this:
-
Capture face image
-
Extract face embedding
-
Compare embedding with stored templates
-
Return match score
But there is a fundamental privacy risk:
-
The server can see raw images or embeddings
-
Stored biometric templates can be accessed if database security fails
-
Insider threats can access sensitive biometric data
-
Cloud services may not satisfy privacy regulations
With HE, the workflow becomes entirely secure.
5. Homomorphic Encryption for Face Recognition (Step-by-Step)
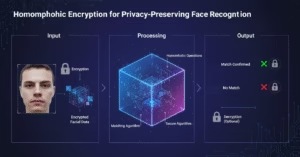
Homomorphically encrypted face recognition modifies the workflow to ensure absolute privacy.
Step 1: Client-side Encryption
The user’s face embedding is encrypted using their public key.
Example:
Embedding vector E → Encrypted embedding E’
Now E’ is impossible to reverse-engineer.
Step 2: Server-side Comparison (on encrypted data)
The server compares E’ with encrypted database embeddings (E1′, E2′, E3′, …)
Operations like:
-
Dot products
-
Subtractions
-
Distance calculations
-
Thresholding
…are all done on encrypted data.
Step 3: Encrypted Result
The result (match score) is encrypted and returned to the client.
Step 4: Client-side Decryption
Only the end-user (client) decrypts the result.
6. Why This Matters for Face Recognition
Homomorphic Encryption fundamentally changes privacy and security in biometric systems.
6.1 Face images never leave the device
Only encrypted vectors are transmitted.
6.2 Biometric databases become useless to hackers
Even if leaked, all data is encrypted with user-specific keys.
6.3 Service providers cannot see or misuse biometric data
Ideal for companies requiring strict privacy separation.
6.4 Zero trust architecture
Servers operate blind, never seeing private information.
6.5 Full regulatory compliance
Including GDPR’s most restrictive biometric processing rules.
6.6 Cloud-based face recognition becomes truly secure
Even hyperscalers cannot read decrypted data.
7. Applications of Homomorphic Encryption in Faceplugin’s Technology
Faceplugin integrates HE into several major systems:
7.1 Encrypted Face Matching
Compares encrypted face embeddings without revealing identities.
7.2 Encrypted User Enrollment
Users enroll privately without exposing biometrics to servers.
7.3 Privacy-Safe Liveness Detection
Liveness signals (eye movement, texture patterns) can be encrypted.
7.4 Secure Multi-Party Computation (MPC) Integration
Faceplugin combines HE with MPC for high-security authentication.
7.5 Encrypted AI Inference
Neural networks operate on encrypted data.
8. Homomorphic Encryption vs Traditional Encryption
| Feature | Traditional Encryption | Homomorphic Encryption |
|---|---|---|
| Data must be decrypted before use | Yes | No |
| Server sees data | Yes | No |
| Insider threat risk | High | Very low |
| Regulatory compliance | Moderate | Maximum |
| Computation on encrypted data | Limited | Fully supported |
| Suitable for biometrics | Risky | Highly secure |
9. Real-World Use Cases
9.1 Banking & Financial Services
Encrypted biometric KYC.
Face verification without revealing face data.
9.2 Healthcare
Protect sensitive patient identity in hospitals.
9.3 Government
Face recognition with absolute citizen privacy.
9.4 Enterprise Workforce
Privacy-preserving attendance and access control.
9.5 Cloud Identity Providers
Enabling SaaS authentication under GDPR constraints.
10. Why Homomorphic Encryption Matters for the Future of AI
AI systems require large-scale data, but users increasingly demand privacy.
Homomorphic Encryption empowers:
10.1 Cloud AI without trust barriers
Computation is safe even in untrusted environments.
10.2 Decentralized identity systems
Self-sovereign identity with encrypted biometrics.
10.3 Secure federated learning
Training AI models across organizations without sharing raw data.
10.4 AI democratization
Companies can collaborate securely.
11. Challenges of Homomorphic Encryption (And How Faceplugin Solves Them)
Homomorphic Encryption is computationally heavy.
Faceplugin addresses challenges using:
11.1 Optimized encryption schemes
Using CKKS, BFV, and proprietary hybrid models.
11.2 GPU-accelerated HE
Significant speed improvements.
11.3 Compressed encrypted embeddings
Reducing computational load by up to 80%.
11.4 Approximate distance calculations
Enabling real-time face matching.
11.5 On-device processing
Minimizes server requirements.
Faceplugin’s research lab continues pushing boundaries in high-speed encrypted computation.
12. Example: How Encrypted Face Recognition Works (Technical Deep Dive)
Let’s break down a typical matching pipeline.
12.1 Face Embedding Vector
Embedding = [e1, e2, e3, …, eN]
N = 128, 256, 512 dimensions depending on model.
12.2 HE Encryption
Each element is encrypted individually or as a polynomial batch.
12.3 Distance Calculation
Commonly L2 or cosine distance.
Under HE:
Where E’ and D’ are encrypted values.
12.4 Thresholding
Server computes:
12.5 Client decrypts result
Only the client holds the private key.
No face data is ever exposed.
13. Homomorphic Encryption in On-Premise vs Cloud Deployment
13.1 On-Premise
-
Maximum data control
-
Ideal for banks, governments, hospitals
-
HE further strengthens internal security
13.2 Cloud
-
Enables face recognition securely at scale
-
No raw biometric data stored
-
Even cloud operators cannot see data
13.3 Hybrid
-
Embeddings encrypted on-prem
-
Compared in the cloud
HE makes every deployment model secure.
14. Integration With Faceplugin SDKs
Faceplugin provides cross-platform SDKs supporting encrypted biometric workflows.
14.1 Mobile SDKs
-
React Native
-
Flutter
-
Swift iOS
-
Kotlin Android
-
.NET MAUI
-
Ionic/Cordova
14.2 Web SDKs
-
JavaScript
-
React
-
Vue
14.3 Server SDKs
-
Linux
-
Windows
-
Docker
-
Kubernetes
Homomorphic Encryption can be integrated into any of these pipelines depending on architecture.
15. Security Benefits
15.1 Protection Against Database Breaches
Encrypted templates = useless to hackers.
15.2 Protection Against Insider Attacks
Employees cannot misuse data.
15.3 Zero Knowledge Processing
Service providers never see biometric data.
15.4 Cryptographic Strength
Based on lattice-based post-quantum schemes.
15.5 Long-Term Privacy Preservation
Even decades later, encrypted data remains safe.
16. Regulatory Benefits
Face recognition is heavily regulated.
HE ensures compliance with:
-
GDPR (Biometric Processing)
-
CCPA
-
ISO/IEC 24745
-
HIPAA (Health Data)
-
PSD2 (Financial Authentication)
-
DPA (Regional privacy laws)
HE enables companies to legally operate face recognition where raw biometric storage is restricted.
17. Future of Privacy-Preserving AI With Faceplugin
Faceplugin envisions a future where:
-
All face recognition is encrypted by default
-
Users control their biometric identity
-
AI systems operate safely in untrusted environments
-
Privacy and performance exist together
-
Cloud-based AI is secure for everyone
Homomorphic Encryption is a pillar of this direction.
18. Conclusion: Why Homomorphic Encryption Is the Future of Face Recognition
Homomorphic Encryption represents one of the greatest advances in cryptography and AI security in decades. It allows organizations to offer AI-powered face recognition—without ever compromising privacy.
With HE, companies can:
-
Perform face matching without decrypting data
-
Secure biometric templates even in the cloud
-
Build zero-trust authentication systems
-
Ensure regulatory compliance
-
Protect user identity at a cryptographic level
Faceplugin’s cutting-edge research brings this technology into real-world applications, enabling enterprises to deploy face recognition safely, ethically, and at global scale.
Homomorphic Encryption is not just a new feature—
it is the foundation of the next generation of privacy-preserving biometrics.